Keep informed on the latest trends and updates with InLigo
Custom Power Apps
InLigo’s Power App custom solution empowers businesses with tailor-made applications that streamline operations, enhance productivity, and revolutionize the way your business works.
AI Copilot – Custom App Development
Unleashing the Potential of AI Copilot: Discuss the capabilities of AI Copilot within the custom app. AI Copilot is a new feature in Microsoft 365 that combines the power of large language models (LLMs) with [...]
Seamless CRM Integration with Microsoft Dynamics 365 and Custom App Development
Seamless CRM Integration with Microsoft Dynamics 365 and Custom App Development. In the ever-evolving business landscape, customer relationship management (CRM) has emerged as a vital tool for organizations looking to cultivate meaningful relationships with their [...]
Custom App Development
Streamlining Operations in Vertical Industries: Unleashing the Power of Custom App Development In today's fast-paced business landscape, vertical solutions have emerged as a critical factor for success across diverse industries. These industry-specific solutions are designed [...]
Case Study – McCleskey Mausoleum
In this case study, we will explore how InLigo assisted a client operating in the construction industry vertical, specifically McCleskey Construction, in effectively managing their daily activities at job sites and streamlining their reporting processes. [...]
Microsoft 365 Security
Robust security solutions and services in Microsoft 365 Security so that you can better protect your enterprise across attack surfaces.
Microsoft Defender: A Comprehensive Guide
Microsoft Defender: A Comprehensive Guide. Microsoft Defender is a suite of security tools that protects your Windows devices from various threats, such as malware, ransomware, phishing, and network attacks. In this blog post, we will [...]
Microsoft Defender – Endpoint Protection
Stay Ahead of Threats with Microsoft Defender: A Deep Dive into Endpoint Protection. InLigo's Free Secure Score is a powerful tool that can help safeguard your company from potential cyber threats. [...]
InLigo’s Cybersecurity – Microsoft 365 Secure Score
InLigo security guidelines and Microsoft 365 solutions that help foster your cybersecurity posture. InLigo is a cybersecurity consulting firm that specializes in helping organizations improve their Secure Score. Our team of experts can analyze [...]
Security & Compliance
Staying Ahead of the Game: Navigating Cybersecurity and Compliance in Today’s Digital Landscape.
InLigo’s Cybersecurity – Microsoft 365 Asset Management
Identify the core elements of your cloud ecosystem and develop a security strategy for how to secure them. Schedule an appointment to discuss your security score. [...]
InLigo’s Cybersecurity – Business Environment
Identify the core elements of your cloud ecosystem and develop a security strategy for how to secure them. InLigo understands that effective security policies must be implemented consistently across the enterprise to protect your In [...]
InLigo’s Cybersecurity – Microsoft 365 – Identity Management and Access Control
InLigo's Cybersecurity Framework: Identity and Access Management (IAM) with Microsoft 365 Solutions Identity and Access Management (IAM) Inligo's goal is to help protect your organization by securing access to the connected world for all [...]
InLigo’s Cybersecurity – Data Security
InLigo's Cybersecurity Framework: Microsoft 365 Identity and Data Security for Enhanced Cybersecurity Posture. InLigo understands that effective security policies must be implemented consistently across the enterprise to protect information ecosystems and customers. Security policies [...]
InLigo’s Cybersecurity – Microsoft 365 – Protective Technology
Enhancing Cybersecurity Posture with InLigo's Framework and Microsoft 365 Protective Technology. Protective Technology Protective Technology is part of Microsoft Intune cloud-based endpoint management solution. It manages user access and simplifies app and device management [...]
InLigo’s Cybersecurity – Protection Processes and Procedures
Information Protection Processes and Procedures InLigo security guidelines and Microsoft 365 solutions that help foster your cybersecurity posture. Microsoft Purview Information Protection to help you discover, classify, and protect sensitive information wherever it lives [...]
InLigo’s Cybersecurity – Anomalies and Events
InLigo's Cybersecurity Framework: Microsoft 365 Identity - DETECT Anomalies and Events InLigo security guidelines and Microsoft 365 solutions that help foster your cybersecurity posture. Anomalies and Events An anomaly describes any change in the [...]
InLigo’s Cybersecurity – Security Continuous Monitoring
InLigo's Cybersecurity Framework includes Security Continuous Monitoring, providing reporting on the state of security of your environment. Our security guidelines and Microsoft 365 solutions help foster your cybersecurity posture. Security Continuous Monitoring Continuous audit [...]
InLigo’s Cybersecurity – Detection Processes
InLigo's Cybersecurity Framework includes Microsoft 365 Identity - DETECT, along with our security guidelines and solutions for Microsoft 365, to enhance your cybersecurity posture. Microsoft 365 Cybersecurity Detect is a feature of Microsoft 365 [...]
InLigo’s Cybersecurity – Microsoft 365 Respond
Microsoft 365 Respond: InLigo Security Guidelines and Solutions to Enhance Your Cybersecurity Posture with Microsoft 365 Security Center Feature. Microsoft 365 Respond is a feature within Microsoft 365 Security Center that helps organizations to [...]
InLigo’s Cybersecurity – Cybersecurity Communications
InLigo security guidelines and Microsoft 365 solutions that help foster your cybersecurity posture. Cybersecurity Communications Microsoft 365 cybersecurity communications refers to the guidelines and procedures for communicating with stakeholders about cyber security issues within [...]
InLigo’s Cybersecurity – Microsoft 365 Analysis
Microsoft 365 Cybersecurity Analysis: InLigo's Security Guidelines and Solutions to Foster Your Cybersecurity Posture. Microsoft 365 cybersecurity analysis is the process of examining an organization's cybersecurity posture and identifying areas for improvement. This may [...]
InLigo’s Cybersecurity – Improvements
InLigo security guidelines and Microsoft 365 solutions that help foster your cybersecurity posture. There are several improvements that organizations can make to their Microsoft 365 cyber security posture: Implement multi-factor authentication: Multi-factor authentication requires [...]
InLigo Cybersecurity – Microsoft 365 – Recovery
Microsoft 365 Cybersecurity Recovery: InLigo's Guidelines and Solutions to Enhance Your Security Posture. Microsoft 365 cybersecurity recovery refers to the process of restoring an organization's systems and data following a security incident. This may involve [...]
NIST Compliance
Ensuring NIST Compliance: A Guide to Microsoft 365's Key Controls and Tools In today’s digital landscape, ensuring compliance with industry standards and regulations is of utmost importance for organizations. The National Institute of Standards and [...]
NIST Compliance
NIST Compliance In today's digital landscape, ensuring compliance with industry standards and regulations is of utmost importance for organizations. The National Institute of Standards and Technology (NIST) provides a comprehensive framework to guide organizations in [...]
Mobile Device Management (MDM)
Staying Informed: monitor, manage, and secure mobile devices remotely.
Microsoft MDM Simplifies Device Management in the Hybrid Workplace
How Microsoft MDM Simplifies Device Management in the Hybrid Workplace. The emergence of the hybrid workplace has become a new normal for many organizations worldwide. The hybrid workplace model combines remote work and in-office work, [...]
The Power of Microsoft MDM
The Power of Microsoft MDM: Unlocking Enterprise-Level Security. Over the years, mobile device management (MDM) has evolved and become increasingly critical in protecting organizations from cyber threats. In today's digital landscape, where remote work and [...]
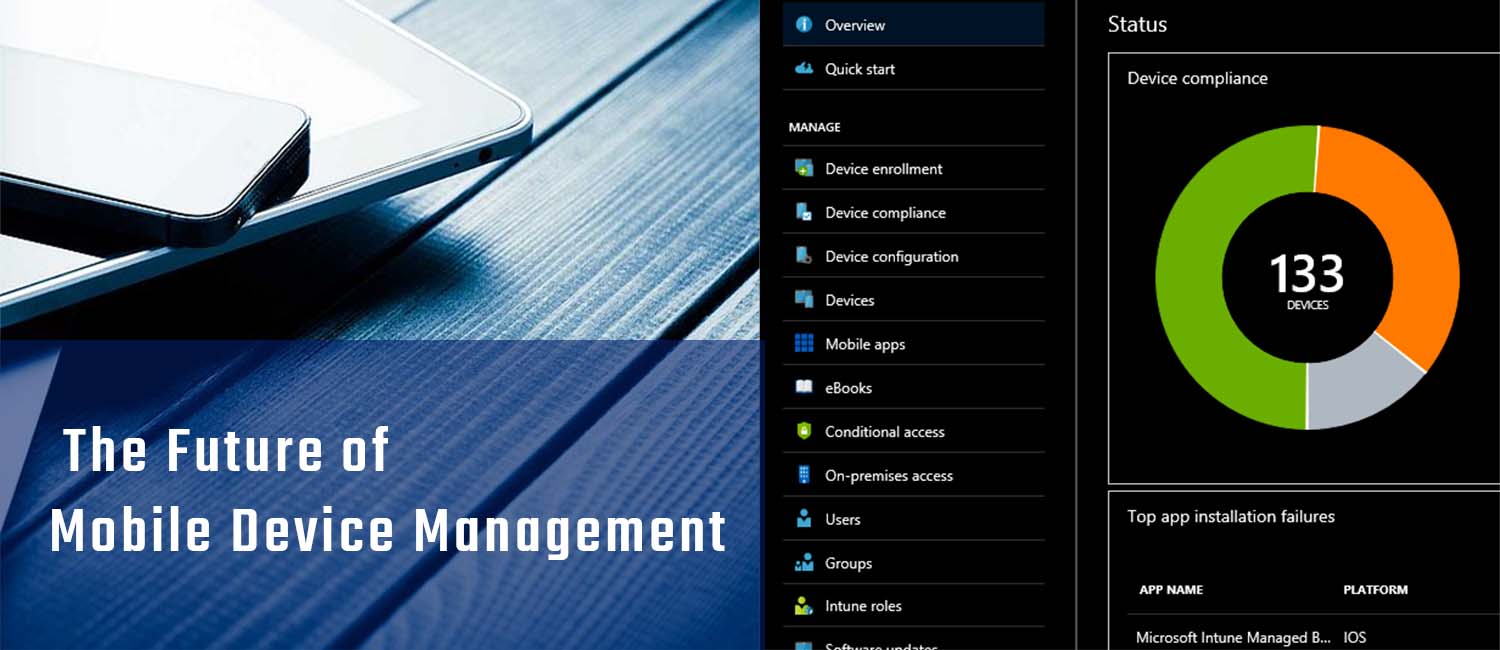
Future of Mobile Device Management
Navigating the Future of Mobile Device Management Latest Trends and Challenges As the world becomes increasingly mobile-centric, the need for effective Mobile Device Management (MDM) solutions has never been more critical. From smartphones and [...]